To take a break from my personal hacking on CD rippers and jukeboxes, I wanted to hack a little on a Flumotion feature.
Now the feature in question was thought up years ago, just like many features we have. Our problem has never been 'what should we implement', it's always been 'in what order do we implement all the things we could do ?'
Anyway, this particular feature is the idea of being able to request a live stream, but going back in time. So instead of seeing what is on now, you could ask to see what was on 30 minutes ago. And you'd connect, get data from that point back in time, then continue as if it was a live stream.
I of course think all my ideas are great, without question. And I've learned to accept over time getting older that everyone else doesn't realize, and so doesn't pick up on these great ideas I'm having. (Who was it again that said irony doesn't work on the internet ?)
Yesterday, in a boss meeting, I was asked to come up with reasons why we stream over HTTP and not over other protocols. I casually threw in a 'you know, we could do crazy things like rewinding in a live stream, or showing what was on half an hour ago.' Which drew a 'hm, that's interesting' from my boss, instead of a usual grunt while he's typing away on his MacBook and fielding a call on his iPhone.
Today, our product manager mails me and says he heard from our boss about this idea, and told me that would be a killer feature to have. So I dutifully replied to some questions he had.
Now, these days, our development process is a bit more structured, so I have two ways of seeing if this can actually work. I can either create a ticket, draft up some requirements, get it on a roadmap for a development cycle, and work with a developer on the team to explain and help out and maybe have something in a few months.
Or, I could just prototype it myself to see if it works, and go the Far West way!
Coming back tonight from tango class, I had been thinking on how I would actually implement it, and started hacking it in as a proof of concept. Basically, I wanted to extend the burst buffer of multifdsink (the GStreamer element responsible for doing the actual streaming) to, say, an hour, and parse a GET parameter like 'offset' in the HTTP request to start bursting from that time offset in the stream.
An embarassing multifdsink bug fix and some flumotion mutilating later, I have this to show for my evening:
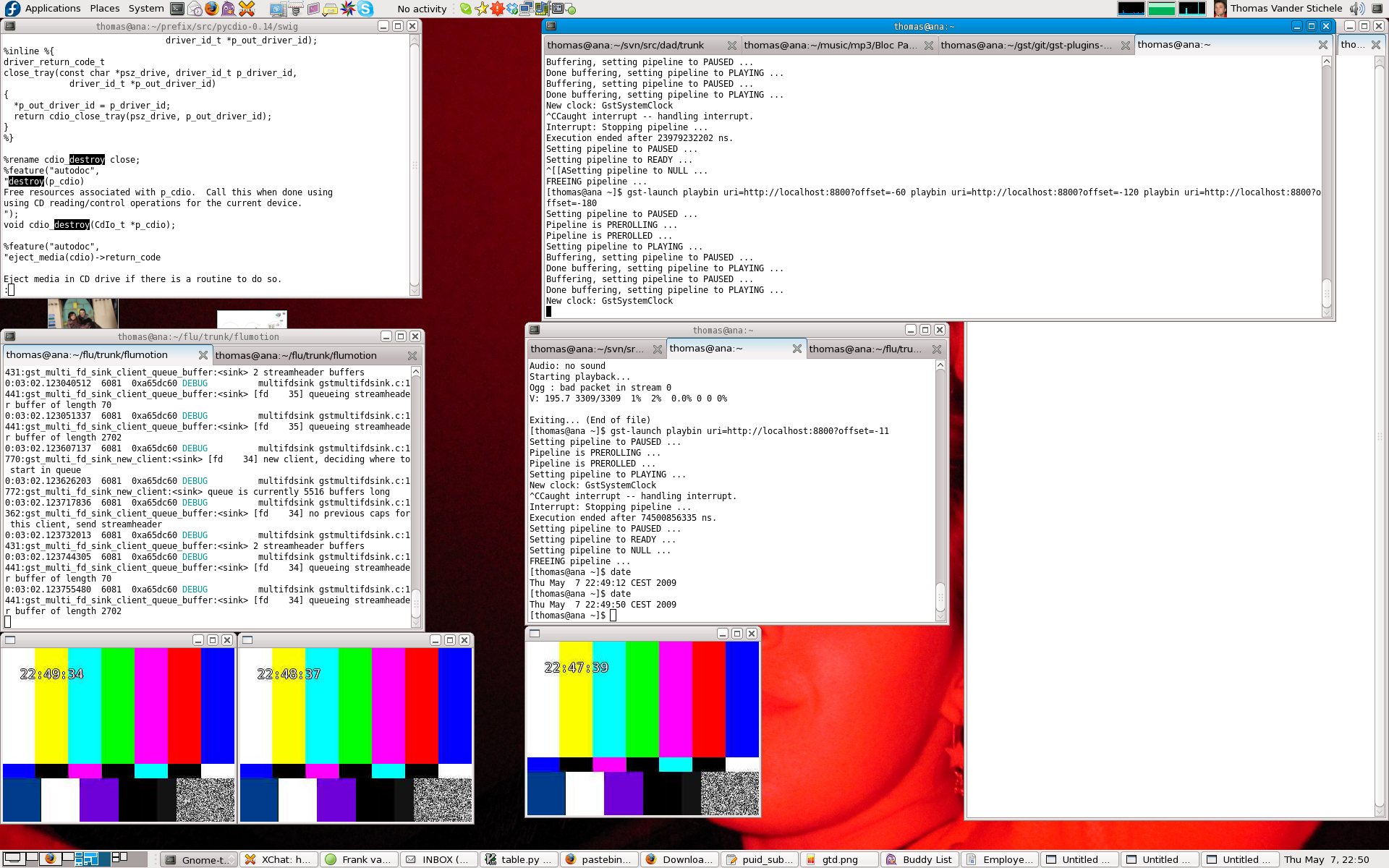
While it doesn't look that exciting, the screenshot shows a flumotion-launch pipeline, and a gst-launch pipeline with three playbin's playing the same live stream, but each with a different offset (a minute away each).
The 3 playback windows thus show 3 streams, roughly offset by a minute from each other. The time displayed is the system time at the time of frame generation. The slight difference from the requested offset is due to the fact that the streams start at a keyframe.
Not bad for a night of hacking.
Now, to actually get this nicely integrated, productized, supportable, and deployed on our platform is another matter. But now I can package up the ugly bits of hacks I did and hand it off to the team for analysis.
Maybe this is what our development manager meant when he said I should go back to hacking Flumotion once in a while?
To take a break from my personal hacking on CD rippers and jukeboxes, I wanted to hack a little on a Flumotion feature. Now the feature in question was thought...
![[lang]](/images/eye.png)
